As we all know many organizations use the standard Lockout policies to ensure the compliance. So this policies are the security majors to ensure that there is no unauthorized access in the network/system. Let’s Understand what is causing Active directory user account frequently locking out. (Ad user Account getting locked out)
There are few question need to understand before drilling down to the problem.
- What is causing user account frequent lockout?
- Where user account frequent getting locked-out from?
- What can I do to fix user account frequent lockout?
- How to find out from Powers shell AD user account frequent lockout?
- If the above steps did not work how to configure AD account frequently lockout in group policies and prevent business impact next time?
- Tools which can be used to find out Ad user Account getting locked out | Account Lockout and Management Tools
What is causing user account frequent lockout?
This is the frequent issue raised by the users and it may be sometimes annoying. So let’s understand what are the key areas we should look for to resolve the issue. There are a few things you will need to look into before going to resolution. First check-in your environment if there are Application servers or systems installed for example. We have installed SAP, Outlook, SQL, DATABASE or other applications installed over the network. Since we can save the password on these applications and it may be stored over the application database. We can look into this application if the password is saved we must clear the passwords or sometimes windows credentials manager will keep the password saved. Hence You have to remove those saved passwords. (Ad user Account getting locked out)
- Whenever a user account authentication is attempted, the credentials are sent up to the acceptable domain controller for the client system’s subnet.
- If the password is wrong which you are trying, the client system’s domain controller forwards the request to the DC holding the PDC emulator role. this is often because the client system’s domain controller won’t have the foremost current password, and as a design feature of Active Directory, the domain controller holding the PDC emulator role always will.
- The PDC emulator tries the password again, and if it’s still found to be wrong, the PDC emulator increments the badPwdCount attribute on the user account.
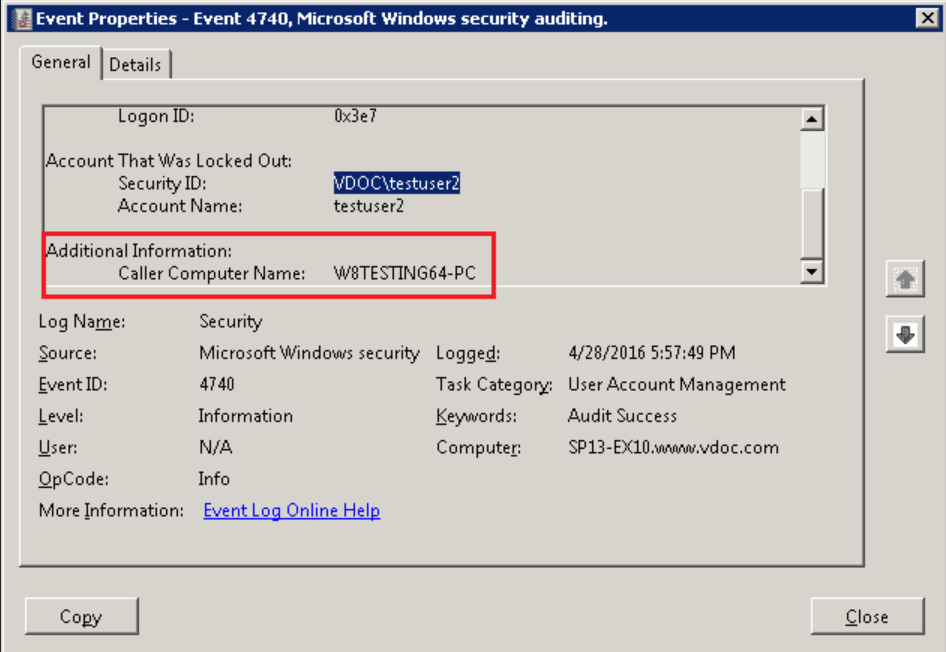
- an occasion ID 4740 is generated on the PDC emulator with the client system IP address that initiated the first request and with the user account.
- The PDC emulator then responds the client system’s domain controller that the password is wrong.
- The client system’s domain controller then notifies the client system that the password was wrong, Hence Lock out the user.
Where user account frequent getting locked-out from?
To understand where exactly the account is stuck frequently we should know what caller computer name is? the caller computer name is where the logon attempts occurred. Hence when a user tries to login, it will basically look into all over the network and search for a database to attempt to grab login details. when a user tries to login & tries to find the login details are correct over a network from the database. if any password was saved anywhere and user found the saved database before the AD database, as the saved database was having an old password. Hence the user will get locked out by multiple wrong attempts.
What can I do to fix user account frequent lockout?
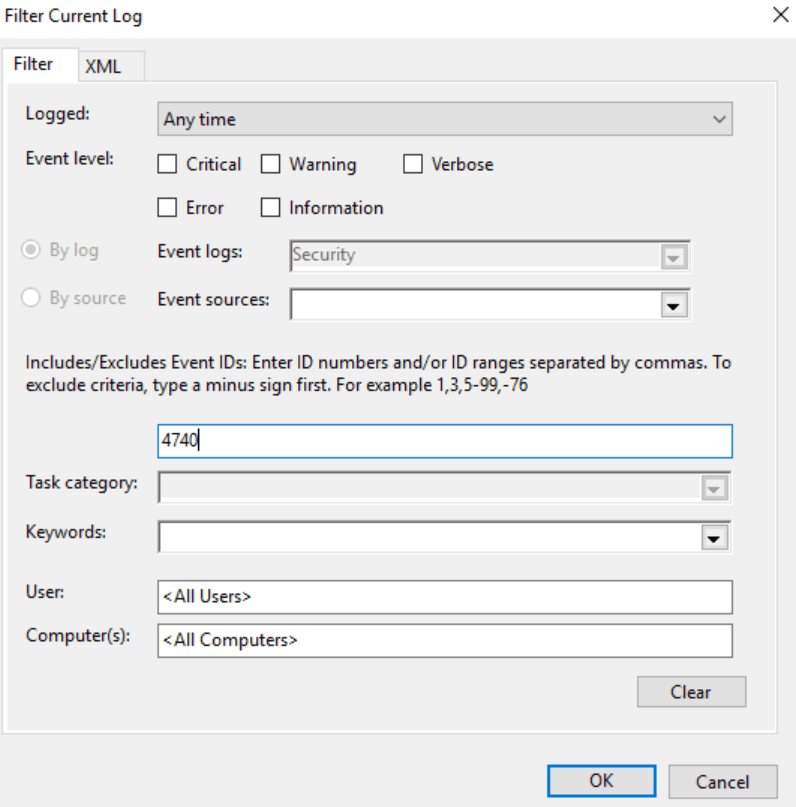
There are a couple of things you can do to fix the issue. First login to the server and open the event viewer (Win+r type eventvwr). Then click on right side panel you will find an option called filter and click on it and the filter window will come. Enter the event id 4740 Note that security event 4740 A is generated when the user account was locked out. This event is generated every time a user account is locked out. PDC emulator is the best place to find out the lockout the source. (Ad user Account getting locked out)
Hence this will give you the caller computer name as mentioned above in figure 1.1.
Checklist to resolve the user account frequently lockout issue | Steps to solve the user account frequently lockout issue | Ad user Account getting locked out
- Check If a Local User Account is the same as the AD account name. If the same ID is available, then rename local ID to some other User name.
- Clear Temporary Files Start -> Run -> %temp%
- Start -> Run -> Logs -> Delete all Logs files.
- Delete Cookies | Temp Files | History | Saved passwords | Forms from all the browsers.
- Start -> Run -> Temp -> Delete all temp files.
- Start –> Run –> Prefetch –> Delete all Prefetch files.
- Remove any Mapped Drives from the computer. My Computer -> Right-click on the particular Shared drive –> click on Disconnect
- Remove stored passwords from Control Panel Run -> Control ->Windows credential manager ->Delete all stored passwords.
- Remote the unwanted applications from StartUp windows (Run –> Msconfig –> startup –> Uncheck unwanted software)
- Check the third-party software installed on client-side. Try to clear the saved passwords on that.
- If the user’s account acts as a service account, update the latest password in service. Ad user Account getting locked out
How to find out from Powers shell AD user account frequent lockout?
Use the following cms in power shell to find our the lockout the source.
Note: This script has not been verified by Digi Networks personally. Please understand the risks before using it or lab it before use.
Import-Module ActiveDirectory
$UserName = Read-Host "Please enter username"
#Get main DC
$PDCEmulator = (Get-ADDomainController -Filter * | Where-Object {$_.OperationMasterRoles -contains "PDCEmulator"})
#Get user info
$UserInfo = Get-ADUser -Identity $UserName
#Search PDC for lockout events with ID 4740
$LockedOutEvents = Get-WinEvent -ComputerName $PDCEmulator.HostName -FilterHashtable @{LogName='Security';Id=4740} -ErrorAction Stop | Sort-Object -Property TimeCreated -Descending
#Parse and filter out lockout events
Foreach($Event in $LockedOutEvents)
{
If($Event | Where {$_.Properties[2].value -match $UserInfo.SID.Value})
{
$Event | Select-Object -Property @(
@{Label = 'User'; Expression = {$_.Properties[0].Value}}
@{Label = 'DomainController'; Expression = {$_.MachineName}}
@{Label = 'EventId'; Expression = {$_.Id}}
@{Label = 'LockoutTimeStamp'; Expression = {$_.TimeCreated}}
@{Label = 'Message'; Expression = {$_.Message -split "`r" | Select -First 1}}
@{Label = 'LockoutSource'; Expression = {$_.Properties[1].Value}}
)
}}
If the above steps did not work how to configure AD account frequently lockout in group policies and prevent business impact next time?
Learn from below websites how to configure policy.
- How to configure account lockout policy for a domain on Windows Server
- Get Active Directory Account Lockout Source Using Powershell
Tools which can be used to find out Ad user Account getting locked out
- Account Lockout and Management Tools
- Netwrix Account Lockout Examiner
- Troubleshooting account lockout the PSS way
Fixed: AD user Account getting locked out frequently? – Complete Guide 2021
Share this content:
Leave a Reply